- Openssl Generate 4096 Bit Key Fob
- Openssl Generate 4096 Bit Key Code
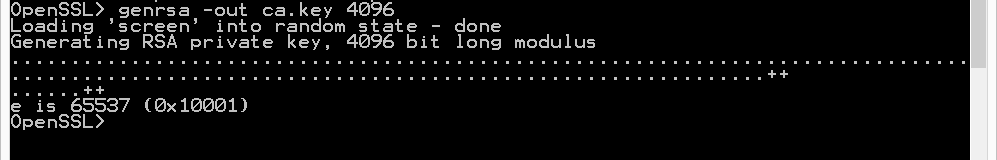
- Openssl Generate Rsa 4096 Key
- Openssl Generate 4096 Bit Key Free
All of the above factors contribute to the increased time it takes to generate larger keys, however this aside, it sounds like this library just isn't particularly fast. Using OpenSSL on a reasonably modern PC I can generate a 2048 bit key in 1 second and a 4096 bit key in. NOTE: All certificates must have at least a 2048 bit key size. 2048 is the industry standard. However, 4096 may be used if the environment requires a larger key size. To generate a 4096 bit key, substitute 4096 for 2048 in the commands below.
I'm trying to generate a 4096-bit DH key, but it has taken over 24 hours and the key is still trying to generate. Can I make this faster?
2 Replies
You're probably not generating enough entropy on your guest. Try generating system activity, like writing to the disk.
You can also use a program like haveged. I won't speak of the security implications as that's a much more complicated subject, but you should know there could be some.
Diffie-Hellman keys can take a long time to generate because dhparam requires something known as a strong prime. Strong primes provide little to no security benefit but take a lot of effort to produce.
Instead, you should be using the -dsaparam option to decrease generation time by avoiding strong prime effort. Here's an example of that:
Openssl Generate 4096 Bit Key Fob

openssl dhparam -dsaparam -out dhparam2.pem 4096
Openssl Generate 4096 Bit Key Code
You can read more about this in the following OpenSSL manpage where you'll find:
-dsaparam
If this option is used, DSA rather than DH parameters are read or created; they are converted to DH format. Otherwise, 'strong' primes (such that (p-1)/2 is also prime) will be used for DH parameter generation.
DH parameter generation with the -dsaparam option is much faster, and the recommended exponent length is shorter, which makes DH key exchange more efficient. Beware that with such DSA-style DH parameters, a fresh DH key should be created for each use to avoid small-subgroup attacks that may be possible otherwise.
Openssl Generate Rsa 4096 Key
There's some additional discussion on this topic here, as well:
https://security.stackexchange.com/questions/95178/diffie-hellman-parameters-still-calculating-after-24-hours